SMAOT500B User Manual
by John Serratusell
Copyright © 2023-2026 Smartjac
Nordic AB
All rights reserved.
Table of contents
The Introduction of USIM and Java Card Technology 6
Evolution to 5G with SMAOT500 Series 6
Ideal User Groups for Smartjac SIM Cards 7
1. Authentication Algorithms 8
2. Shared or application-specific keys 8
2. Identities 9
2. Authentication keys – K/OPc 11
3. SMAOT500B general technical features 14
1. Disabling DF_5GS files and services 16
1. Disabling the ISIM functionality 17
Use Case – Subscriber
Privacy 18
Use Case – Enhanced
Steering of Roaming (SoR) Service 19
Use Case – 5G Private
Networks 19
Use Case – Non-3GPP
Network Access 19
Use Case – V2X in 5G
Network 19
Use Case – Ensuring Good
Quality of Experience 19
Use Case – Network
Resource Optimization 20
2. 5G Parameter description 20
2. SUCI Calculation Information 21
1. Default SUCI data on SMAOT500B 23
Explanatory of the SUCI
sample data: 24
2. Generating SUCI keys with Python 25
5.C.1 URSP User Equipment Route Selection Policy 27
1.
SMAOT500B default content 28
3.
Bibliography / References 49
Table of figures
Figure 1 - SMAOT501B234FF - SMAOT500B type with XOR
algorithm and trio format 5
Figure 2 - White non-printed SIM card
[SMATO500B234FF] 10
Figure 3 - Technical features 14
Table of tables
Table 1 - Default verification codes 10
Table 2 - default card manager keys 15
Table of codes
Code 1 - APDU verification code 11
Code 2 - default authentication key K content 11
Code 3 - default authentication key OPc content 11
Code 4 -sample authentication key OP content 12
Code 5 - Python code to calculate CRC XModem 13
Code 6 - SUCI data sample 1 22
Code 7 - SUCI data sample 2 22
Code 8 - Default SUCI data on SMAOT500B 24
Code 9 - Python code to generate SUCI keys 25
Introduction
The SMAOT500B is a
state-of-the-art 5G UICC SIM card designed for use in 5G, 4G, and legacy
networks. This manual serves as a comprehensive guide for network operators who
utilize Smartjac’s SIM cards for subscriber authentication and secure
communication in modern cellular networks.
The SMAOT500B is an advanced SIM
solution tailored for operators focused on 5G services. It provides enhanced
security features such as Subscriber Privacy Protection (SUCI), on-card SUCI
calculation, User Equipment Route Selection Policy (URSP) for network slicing,
and dual activation support for both Milenage and TUAK authentication
algorithms.
This manual will guide you
through the card’s features, its provisioning process, and how to manage
authentication keys like Ki and OPc.
Please note however, that unless
you have a specific support contract with Smartjac on said configuration,
Smartjac will not be able to help you with questions regarding the use of
SMAOT500B, particularly configurations not described in this manual.

Figure 1 - SMAOT501B234FF - SMAOT500B type with XOR algorithm and trio
format
History
Smartjac began selling a range of
SIM cards in 2005. These early cards were provided in small quantities to meet
the specific needs of customers who required customized SIM cards for test and
research purposes. The cards were pre-programmed with individual identities and
specific test keys such as IMSI, MSISDN, ICCID, authentication keys and PLMN
data. Initially, Smartjac sourced these cards
from Gemplus (which later became
Gemalto and is now part of Thales), providing a reliable platform for customers
in need of test SIM’s.
Over time, customer demands grew
beyond test cards. Requests for specific parameters, such as IMSI ranges and
unique PLMN configurations, prompted Smartjac to introduce full personalization
services. These services allowed customers to order SIM cards pre-configured
with their desired network parameters, while maintaining flexibility for
testing and deployment purposes.
The Introduction of USIM and Java Card Technology
In 2010, Smartjac took a
significant step forward by launching
the SMAGT and SMAOT series of
cards. Unlike their SIM-only predecessors, these were USIM cards, designed
specifically for 3G networks. They supported mutual authentication as part of
the UMTS AKA (Authentication and Key Agreement) protocol, providing enhanced
security features for network authentication.
The SMAOT and SMAGT cards were
also the first Java SIM cards introduced by Smartjac, marking a shift towards
more programmable and versatile SIM technology. This allowed customers to:
·
Develop
and run their own Java Card applets,
·
Utilize
remote file management to update SIM card files over-the-air,
·
Implement
more complex security and service applications directly on the SIM.
By
2015, Smartjac had further advanced its offering by introducing ISIM (IP
Multimedia Services Identity Module) applications, specifically for IMS and
VoLTE (Voice over LTE) services, and PKCS15 applications, adding secure
cryptographic key storage functionality.
Evolution to 5G with
SMAOT500 Series
In
2019, Smartjac introduced the SMAOT500A, which built on the features of
previous cards but was specifically designed to support 5G, 4G LTE and 3G
networks with enhanced security features. However, the rapid pace of
technological advancement necessitated a further update. By 2021, Smartjac
launched the SMAOT500B to address the end-of-life status of both the chip and
the operating system used in the SMAOT500A and also
introduced support for BER-TLV files in order to
support URSP.
The SMAOT500B
The
SMAOT500B is nearly a feature-complete successor to the SMAOT500A, with notable
improvements:
o
Full
support for 5G deployments, offering enhanced privacy and
security
features such as SUCI (Subscription Concealed Identifier) for IMSI encryption , network slicing capabilities and URSP support.
o
Backward
compatibility with legacy networks, including GSM, UMTS, and LTE, making it a
versatile solution for various network environments.
o
Dual
activation of Milenage and TUAK algorithms, ensuring compliance with a range of
operator authentication protocols.
Ideal User Groups
for Smartjac SIM Cards
All
these features make the SMAOT500B, ideal for a wide range of users:
o
Small
operators running local or regional cellular networks across technologies like
GSM, GPRS, EDGE, UMTS, HSPA, LTE, and now 5G.
o
Private
networks, both small and medium in scale, that require flexible, customizable
SIM solutions.
o
Researchers
and developers focused on SIM security, STK (SIM
ToolKit) applications, and other
advanced mobile network technologies.
1. Authentication Algorithms
A GSM
network can support any authentication algorithm as long as
it is implemented in both the SIM/USIM and the Authentication Center (AUC) of
the operator. Operators are free to choose their preferred algorithm for
subscriber authentication, but implementing custom algorithms may require
significant cryptographic expertise and resources.
To standardize this, the GSMA introduced the
COMP128 family of algorithms,
with COMP128v1, v2, and v3. Only COMP128v3 is
considered secure today, as earlier versions have known vulnerabilities. The
SMAOT500A and SMAOT500B support the full set of COMP128 algorithms for legacy
SIM protocols.
For
USIM and ISIM applications, most networks use the MILENAGE algorithm, which is
widely adopted and supported by the SMAOT500A and SMAOT500B for secure mutual
authentication in modern networks.
1.
OP or OPc in USIM
The
128-bit value OOP is the Operator Variant Algorithm Configuration field, which
was included to provide separation between the functionality of the algorithms
when used by different operators. It is left to each operator to select a value
of OP. The algorithm set is designed to be secure whether or
not OP is publicly known; however, operators may see some advantage in
keeping their value of OP secret as a secret OP is one more hurdle in an
attacker’s path.
The
USIM can be configured to either store an OP value, or an OPc value. OPc is
computed by XOR of OP and EK(OP). So the operator and
card-issuer has the choice to either:
§ use one OP value all
across his network, and store that value on each card, or
§ pre-compute a card-specific OPc value, and
store that individual OPc on each card
The latter choice (OPc on card) is generally
considered more secure, as the reverse engineering of one OPc does not reveal
any security parameters relevant beyond that single card.
The
SMAOT500B support storing either the card-individual OPc as well as the global
OP value and thus gives maximum flexibility to the user.
For
more details on OP and OPc as well as the rationale for preferring OPc storage
on the card, see Section 5.1 of 3GPP TS 35.206 [3gpp-ts-35-206] as well as
Section
8.3 of 3GPP TS 35.205 [3gpp-ts-35-205].
2.
Shared or application-specific keys
Card
with multiple applications, such as the SMAOT500B containing SIM, USIM and ISIM
applications can either
§
use
shared keys for all of those applications, meaning
that one set of K and OP/OPc is used for
authentication to any of those applications, or
§
use
separate keys for each of those applications. This would permit separate K and
OP/OPc values for each application, e.g. different keys for authentication of
USIM against the radio network and ISIM against the IMS network
SMAOT500B uses shared keys.
2. Identities
There
are several identities associated with the use of SIM cards.
1.
ICCID
I The
ICCID (Integrated Circuit Card Identifier) is a globally unique serial number
assigned to SIM cards. It follows the format specified by ITU-T in
recommendation
E.118 and is based on the ISO/IEC 7812 standard. The ICCID can be up to 22
digits long, including a Luhn check digit for error detection.
The
ICCID is not transmitted over the radio interface, so it doesn't play a
significant role in the operation of private cellular networks. On Smartjac
cards, the ICCID is typically 20 digits long, consisting of 18 digits, a Luhn
checksum, and an additional 'F' character. The ICCID can be overwritten as
needed.
2.
IMSI
The IMSI (International Mobile
Subscriber Identifier) is a [supposedly] globally unique number of the
subscriber of 3GPP network technology. The number must be unique in public
networks, but not necessarily so in private networks.
The
first 5-6 digits of the IMSI are typically comprised by the MCC (Mobile Country
Code) and MNC (Mobile Network Code). The MCC specifies the country, and the MNC
the card-issuing network within the country.
MNCs are assigned by the
respective national telecommunications regulatory
authority. The policies differ from country to country, but typically you have to be a licensed mobile network operator (with your own
spectrum allocation) in order to receive a MCC
allocation and hence be able to issue your own IMSIs within your MCC-MNC.
As
Smartjac is not a telecom operator we do not have our own MCC/IMSI allocations
- neither can we get one.
The
default IMSIs pre-provisioned on our “blank” cards are normally within the MCC-
MNC of 001-01 with the
IMSI: 001010123456789
1.
SMAOT500B specifications

Figure 2 - White
non-printed SIM card [SMATO500B234FF]
1. Verification codes
Table 1 - Default
verification codes
|
Register |
Value (default settings) |
Binary value stored on card |
|
GPIN |
1234, disabled |
31323334FFFFFFFF |
|
LPIN |
5678, enabled |
35363738FFFFFFFF |
|
ADM1 |
11111111 |
3131313131313131 |
|
ADM2 |
22222222 |
3232323232323232 |
Code 1 - APDU
verification code
00A4040C 0C A0000000871002FFFFFFFF89 /SELECT USIM AID
0020000A 08 3131313131313131 /VERIFY ADM1
0020000B 08 3232323232323232 /VERIFY ADM2
00200081 08 35363738FFFFFFFF /VERIFY LPIN
1. Authentication keys – K/OPc
K
stored in:
MF / USIM / 62FC
§
18
bytes
§ 62FC contains K, the network
authentication key, 16 bytes, and checksum 2 bytes
OPc
stored in:
MF / USIM / 62FD
§
104
bytes
§ 62FD contains operator key type byte, Opc,
derived operator key, 16 bytes,checksum 2 bytes and
rotation/constant parameters.
EF_62FC
content:
[K] [CH]
EF_62FD content:
01 [OPc] [CH]
40002040600000000000000000000000000000000000000000000000000000000000000001000000000
00
00000000000000000000200000000000000000000000000000004000000000000000000000000000000
08
Replace
[K] with 16 byte K key & Replace
[OPc] with 16 byte OPc key
Default
data for EF_62FC on card:
Code 2 - default
authentication key K content
|
77 |
77 |
77 |
77 |
77 |
77 |
77 |
77 |
77 |
77 |
77 |
77 |
77 |
77 |
77 |
77 |
A0 33 |
Default
data for EF_62FD on card:
Code 3 - default
authentication key OPc content
|
01 |
DB 46 EE F8 8A 1A 4F 3B B0 5B 1A D8 80 DA 07 F2 |
D2 F7 |
40 00 20 40 60 00 00 |
|
|
00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 |
||||
|
00 00 00 01 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 02 00 00 00 00 00 00 |
||||
|
00 00 00 00 00 00 00 00 00 04 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 08 |
Sample
data for OP in EF_62FD on card:
Code 4 -sample
authentication key OP content
|
00 |
CD C2 02 D5 12 3E 20 F6 2B 6D 67 6A C7 2C B3 18 |
DE FE |
40 00 20 40 60 00 00 |
|
|
00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 |
||||
|
00 00 00 01 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 02 00 00 00 00 00 00 |
||||
|
00 00 00 00 00 00 00 00 00 04 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 08 |
[CH]
is a 2 byte checksum based on the 16
byte Hex code. It has to be calculated both for
K and Opc (or OP).
The
checksum is a CRC calculation. More specifically a CRC-16 polynomial 0x1021
with input/initialization 0000. Also called CRC-16-XMODEM.
Online sample
calculations can be done here (for example to check that your own calculations
are correct): https://www.lammertbies.nl/comm/info/crc-
calculation.html (use the result of CRC-CCITT (XModem))
See
sample Python code on the next page.
The
rest of the EF_62FD contains the Milenage configuraton constants [Ci] and
Rotation values [Ri] where the below default values are provisioned, in
accordance with [3gpp-ts-35-206] Section 4.1.
Parameter Value
C1
00000000000000000000000000000000 C2 00000000000000000000000000000001 C3
00000000000000000000000000000002 C4 00000000000000000000000000000004 C5
00000000000000000000000000000008 R1
0x40 R2 0x00 R3
0x20 R4 0x40 R5 0x60
Code 5 - Python code to calculate CRC XModem
def crc16_xmodem(data:
bytes) -> int: """
Compute the CRC-16-XMODEM checksum of the input
data.
Parameters:
data (bytes): The data to compute the CRC on.
Returns:
int:
The computed CRC value. """
crc
= 0x0000 polynomial = 0x1021
for byte in data: crc ^= byte << 8
for _ in range(8): if crc
& 0x8000:
crc = (crc << 1) ^ polynomial else:
crc <<= 1
crc &= 0xFFFF # Ensure CRC remains 16-bit
return crc
def main():
# Get input from user
user_input = input("Enter
a 16-byte hexadecimal string (32 hex characters):
")
# Validate input
if len(user_input) != 32:
print("Invalid input length. Please enter exactly
32 hex characters (16
bytes).")
return
try:
#
Convert input string to bytes data = bytes.fromhex(user_input)
except ValueError:
print("Invalid hex string. Please enter a valid
hexadecimal string.") return
#
Calculate CRC-16-XMODEM crc_value = crc16_xmodem(data)
# Print the result
print(f"CRC-16-XMODEM Checksum:
{crc_value:04X}")
if name ==
" main ": main()
1. SMAOT500B general technical features
Figure 3 - Technical
features
2. Card manager keys
Table 2 - default
card manager keys
|
ISD Value Max Size |
||
|
%Default_Card_Manager_Key_Set_Enc_Secret_Key |
456E6372797074696F6E53656 3726574 |
16 |
|
%Default_Card_Manager_Key_Set_Mac_Secret_Key |
506572736F6E616C69736174696 F6E4B |
16 |
|
%Default_Card_Manager_Key_Set_Key_Encrypt_Key |
4B6579456E6372797074696F6E4 B6579 |
16 |
2.
USIM cards and 5G
The
5G/NR technology maintains full backward compatibility with existing SIM cards,
meaning that no special updates or functionalities are strictly required for a
USIM to operate on 5G networks. The USIM was originally introduced in 3G/UMTS
Release 99, and with the arrival of 4G and 5G, 3GPP ensured that older SIM
cards would continue to work on these newer networks without issues.
However,
as network capabilities evolved, 3GPP introduced various optional files in
later releases to support advanced use cases, particularly for 5G. The
SMAOT500B includes all optional files specified for 5G up to Release 16. While
the 5G functionality of a USIM is standardized by 3GPP, the SMAOT500B offers
comprehensive support for these files, although the functionality itself is not
unique to this specific card.
Several
5G-related parameters are contained within the USIM, primarily located in the
DF_5GS directory. These files are optional, but to support certain features—
such as the Subscriber Concealed Identifier (SUCI) privacy function—these files
must be present. Given that Smartjac’s products are widely used in test labs,
the SMAOT500B includes most of these optional files. If these files are absent,
features like SUCI cannot be utilized.
By
default, a blank card has UST service 124 disabled. The
SUCI_Calc_Info file (4F07) within DF_5GS will remain hidden unless service 124
is activated, and service 125 (if enabled) is deactivated.
When
these 5G-related files are active, they must contain valid data tailored to the
specific configuration of the network. As Smartjac is not a network operator,
it cannot provide predefined configurations for your network. It is the
responsibility of the network operator to ensure that these files are properly
configured to align with their network settings.
Detailed
specifications for the contents of these files can be found in [3GPP TS
31.102], Section 4.4.11, which outlines the files under the DF_5GS director,
and in the coming section 5 in this document.
1. Disabling DF_5GS files and services
If you
choose not to configure these 5G files with network-specific data, you have the
option to disable them. To do this:
1. Disable the related services from EF.UST
(Services no. 122 through no. 135).
2. If further action is required (since some
UEs may attempt to access these files regardless of EF.UST settings), you can
fully deactivate the relevant files using the DEACTIVATE FILE command, as
specified in [ETSI TS 102 221] Section 11.1.14.
Smartjac
provides SIM cards that adhere to all relevant 3GPP, ETSI, and ISO standards,
ensuring full compliance with industry specifications.
3.
USIM/ISIM cards and IMS
IMS
(IP Multimedia System) is the framework used to handle circuit-switched
services like voice calls over modern 3GPP networks, including LTE/4G, NR/5G,
and Wi-Fi. While IMS can function without explicit SIM configuration, relying
on automatic provisioning and default settings (such as deriving the IMPI from
the IMSI), more advanced configurations can be achieved in two ways:
o
By
including specific files within the ADF.USIM, or
o
By
utilizing a dedicated ADF.ISIM application.
These
two approaches are mutually exclusive: if the ADF.ISIM application is present
on the card, the IMS-related files within ADF.USIM must not be used.
The
SMAOT500B includes the ADF.ISIM application and all 3GPP-specified files up to
Release 16. Therefore, when using the SMAOT500B for IMS, you have two options:
either ensure the card’s IMS configuration aligns with your network's settings
or deactivate the ISIM and fall back on 3GPP’s default configuration.
3. Disabling the ISIM functionality
If you
choose not to configure the IMS-related files to match your network, you can
disable them. To do this:
1. Disable the relevant services within
ADF.USIM/EF.UST.
2. Remove the ISIM application from EF.DIR.
1.
5G Parameter Checklist
|
Legend |
|
|
R//C/AM |
R = SMARTJAC Recommended, C = Customer Discretion – AM = Applet & Mobile Equipment Dependent |
Use Case – Security
|
Feature |
R/C/AM |
Recommended Value |
Customer Value (Requirement) |
|
|
Mobility Management |
R |
UST Service 20 available & Associated Files |
☐ |
|
|
EF User Controlled PLMN selector with Access technology (6F60)= Do not exclude 5G |
||||
|
UST Service 42 available & Associated Files |
☐ |
|||
|
EF Operator Controlled PLMN selector with Access technology (6F61) = Do not exclude 5G |
||||
|
UST Service 43 available & Associated Files |
☐ |
|||
|
EF HPLMN selector with Access technology (6F62) = Do not exclude 5G |
||||
|
UST Service no.122 available & Associated files |
☐ |
|||
|
EF5GS3GPPLOCI (4F01) = 'FFFFFFFFFFFFFFFFFFFFFFFFFF MCC MNC 000000 01’ |
||||
|
EF5GSN3GPPLOCI (4F02) = 'FFFFFFFFFFFFFFFFFFFFFFFFFF MCC MNC 000000 01’ |
||||
|
EF5GS3GPPNSC (4F03) = 'FF…FF' |
||||
|
EF5GSN3GPPNSC (4F04) = 'FF…FF' |
||||
|
C |
UST Service no.129 available. & Associated files |
☐ |
||
|
EFOPL5G (4F08) configured as per project specific (Link) |
||||
|
Secondary keys for value added services |
R |
UST Service no.123 & 133 available & Associated files |
☐ |
|
|
EF5GAUTHKEYS (4F05) present = 'FF…FF' File size is at least 110 bytes |
||||
|
USAT Pairing |
C |
UST Service no.102 available & Associated files |
☐ |
|
|
EFIAL (R18+) / EF IWL (R16+) (6FF0) configured as per project specific (Link) |
||||
|
EFIPS (6FF1) = 'FF…FF' |
||||
|
EFIPD (6FF2) = 'FF…FF' |
Use Case –
Subscriber Privacy
|
Feature |
R/C/AM |
Recommended Value |
Customer Value (Requirement) |
|
|
5GS mobile identity |
R |
SUPI type: IMSI |
|
|
|
Services related to SUPI protection & calculation |
R |
UST Service no.124 & 125 available & Associated files |
☐ |
|
|
EFSUCI_Calc_Info (4F07) configured as per project specific (Link) |
||||
|
EFRouting_Indicator (4F0A) = ‘F0FF0000' |
||||
|
SUCI 5G NSWO context in GET IDENTITY command |
C |
UST Service no.142 available & Associated files |
☐ |
|
|
EF5GNSWO_CONF (4F11) = ‘01’ |
Use Case – Network
Slicing
|
Feature |
R/C/AM |
Recommended Value |
Customer Value (Requirement) |
|
|
User Equipment Route Selection Policy |
C |
UST Service no.132 available & Associated files |
☐ |
|
|
EFURSP (4F0B) configured as per project specific (Link) |
||||
|
Toolkit Support |
AM |
TERMINAL PROFILE bit 4 of byte 36 supported – Network Slicing info PROVIDE LOCAL INFO contains Service PLMN Single Network Slice Selection Assistance Information (S-NSSAI) (Link) |
N/A |
|
|
Closed Access Group |
AM |
PROVIDE LOCAL INFO contains Closed Access Group Id |
N/A |
|
|
C |
UST Service no.137 available & Associated files |
☐ |
||
|
EFCAG (4F0D) configured as per project specific (Link) |
Use Case – Enhanced
Steering of Roaming (SoR) Service
|
Feature |
R/C/AM |
Recommended Value |
Customer Value (Requirement) |
|
|
Steering of Roaming (SoR) over control plane |
C |
UST Service no.127 available |
☐ |
|
|
Steering Of Roaming - Connected Mode Control Information |
C |
UST Service no.138 available & Associated files |
☐ |
|
|
EFSoR-CMCI (4F0E) configured as per project specific (Link) |
||||
|
Toolkit Support |
AM |
TERMINAL PROFILE bit 5 of byte 36 supported – for Refresh SoR CMCI |
N/A |
Use Case – 5G
Private Networks
|
Feature |
R/C/AM |
Recommended Value |
Customer Value (Requirement) |
|
|
Standalone Non-Public Network (SNPN) |
C |
Subscriber Identity: non-IMSI SUPI |
|
|
|
C |
UST Service no.143 available & Associated files |
☐ |
||
|
EFPWS_SNPN (4F01) configured as per project specific (Link) |
||||
|
C |
UST Service no.146 available & Associated files & AID |
☐ |
||
|
EFNID (4F02) configured as per project specific (Link) |
||||
|
C |
USIM AID used non-IMSI SUPI: A000000087 100B |
☐ |
||
|
Public Network integrated Non-Public Network (PNI-NPN) |
C |
Subscriber identity either IMSI or NAI SUPI |
||
|
USIM AID in case of non-IMSI SUPI: A000000087 100B |
☐ |
|||
|
5G Wireline and Wireless Convergence |
C |
Subscriber identity: NAI SUPI contains NSI, GCI, or GLI (Link) |
||
|
USIM AID for non-IMSI SUPI: A000000087 100B |
☐ |
|||
|
NAI SUPI Type Dedicated SUPI Type for private Network Access Identifier (NAI) in 5G network |
C |
UST Service no.130 available |
☐ |
|
|
Subscriber identity: NAI SUPI contains NSI, GCI, or GLI (Link) |
||||
|
USIM AID for non-IMSI SUPI: A000000087 100B |
☐ |
Use Case – Non-3GPP
Network Access
|
Feature |
R/C/AM |
Recommended Value |
Customer Value (Requirement) |
|
|
Trusted non-3GPP network access |
C |
UST Service no.135 available & Associated files |
☐ |
|
|
EFTN3GPPSNN (4F0C) configured as per project specific (Link) |
Use Case – V2X in 5G
Network
|
Feature |
R/C/AM |
Recommended Value |
Customer Value (Requirement) |
|
|
C-V2X technology in 5G Network |
C |
UST Service no.119 available & Associated DF & files |
☐ |
|
|
DFV2X (5F3E) present under DF TELECOM (7F10) |
☐ |
|||
|
EFVST (4F01) configured as per project specific (Link) |
||||
|
EFV2X_CONFIG (4F02) configured as per project specific (Link) |
||||
|
EFV2XP_PC5 (4F03) configured as per project specific (Link) |
||||
|
EFV2XP_Uu (4F04) configured as per project specific (Link) |
Use Case – Ensuring
Good Quality of Experience
|
Feature |
R/C/AM |
Recommended Value |
Customer Value (Requirement) |
|
|
Multi-Device and Multi-Identity |
C |
UST Service no.134 available |
☐ |
|
|
EFMuDMiDConfigData (6FFE) configured as per project specific (Link) |
||||
|
Call control on PDU Session by USIM |
C |
UST Service no.128 available |
☐ |
|
|
Network Rejection Event |
AM |
Allows UICC to retrieve the network rejection codes when network issues prevent connection |
N/A |
|
|
Data connection status Change Event for 5GS |
AM |
Informs UICC that ME has detected a change in 5GS data connection |
N/A |
|
|
Provide Local Information extended to support NG-RAN information |
AM |
ME provides to UICC information on MNC, MCC, LAC/TAC, cell id, NG-RAN cell id |
N/A |
|
|
Timing advance information |
AM |
ME provides UICC with NR primary timing advance |
N/A |
|
|
Network measurement report |
AM |
ME provides UICC with available Network Measurement Report (NMR) related to NR |
N/A |
Use Case – Network
Resource Optimization
|
Feature |
R/C/AM |
Recommended Value |
Customer Value (Requirement) |
|
|
Unified Access Control |
C |
UST Service no.126 available |
☐ |
|
|
EFUAC_AIC (4F06) configured as per project specific (Link) |
||||
|
C |
UST Service no.127 available |
☐ |
2.
5G Parameter description
1.
OPL 5G
OPL 5G stored
under EFOPL5G (4F08) (see 3GPP TS 31.102). It contains the Tracking Area
Identity and PLMN Network Name Record Identifier: <MCC><MNC><TAC><PNN Rec.Id> Example:
Rec.#1: 012345 000000 FFFFFE 01
USAT Pairing
UE-based procedure with USAT application pairing
defined in 3GPP TS 33.187 Security aspects of Machine - Type Communication. It
needs list of allowed IMEI(SV) range of values to be stored in EFIAL (6FF0)
(see 3GPP TS 31.102).
IMEI
|
Length |
Description |
Status |
|
1 byte |
Tag of Range of IMEI values: '80' |
M |
|
1 byte |
Length |
M |
|
X bytes |
IMEI range of values that the USIM is authorized to be paired to |
C |
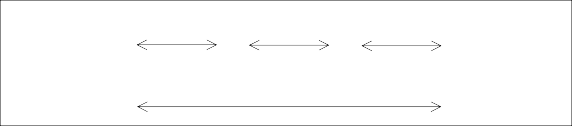
8 digits
6 digits
1 digit
IMEI 15 digits
CD/ SD
SNR
TAC
The IMEI is composed by Type Allocation Code
(TAC), Serial Number (SNR), and Check Digit (CD) / Spare Digit (SD).
IMEISV
|
Length |
Description |
Status |
|
1 byte |
Tag of Range of IMEISV values: '81' |
M |
|
1 byte |
Length |
M |
|
X bytes |
IMEISV range of values that the USIM is authorized to be paired to |
C |
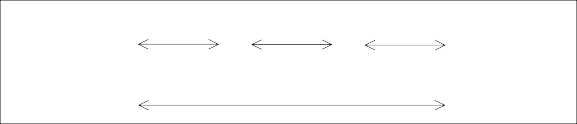
8 digits
6
digits
2
digits
IMEISV 16 digits
SVN
SNR
TAC
The IMEISV is composed by Type Allocation
Code (TAC), Serial Number (SNR), and Software Version Number (SVN).
1.
SUCI Calculation Information
SUCI Calculation Information stored under
EF_SUCI_Calc_Info (4F07) (see 3GPP TS 31.102). Or if the UICC should make the
SUCI calculations, USIM / DF 5FD0 / 4F01 must contain the SUCI data and UST
service 125 be activated.
SUCI_Calc_Info contains the list of Protection
Scheme Identifier and the list of Home Network Public Key.
Protection Scheme Identifier List
The Protection Scheme Identifier represents a
protection scheme as described in 3GPP TS
33.501
and it is coded in one byte as follows:
![]()
![]()
b1
b2
b3
b4
b5
b6
b7
b8
Protection
Scheme identifier coded as described in 3GPP TS 24.501
RFU,
bit = 0

Home
Network Public Key List
It contains a list of the Home Network Public Key
and the corresponding Home Network Public Key Identifier that shall be used by
the ME to calculate the SUCI.
The Home Network Public Key Identifier may have
any value in the range from 0 to 255 as described in 3GPP TS 23.003.
The Home Network Public Key is coded in
hexadecimal digits as described in IETF RFC 7748 (for Protection Scheme Profile
A) and in IETF RFC 5480 (for Protection scheme Profile B). The length of the
Home Network Public Key depends on the Protection Scheme and the form of the
Home Network Public Key (e.g. compressed or uncompressed).
For
example,
Code 6 - SUCI data sample 1
|
A0 04 02010102 \ ; Profile B with key index 1 and profile A with key index 2 |
|
|
A1 |
4B \ ; HN public key list data object |
|
80 |
01 0C \ ; HN public key index 1, Id 0C |
|
81 |
21 02 72DA71976234CE833A6907425867B82E074D44EF907DFB4B3E21C1C2256EBCD1 \ ; |
|
HN |
public key value (compressed) |
|
80 |
01 05 \ ; HN public key index 2, Id 05 |
|
81 |
20 5A8D38864820197C3394B92613B20B91633CBD897119273BF8E4A6F4EEC0A650 \ |
|
; HN public key value |
A0
04 02010102 \
key index 2 A1 6B \
80 01 0C \
;
Profile B with key index 1 and profile A with
; HN
public key list data object
; HN
public key index 1, Id 0C
81
41 04 72DA71976234CE833A6907425867B82E074D44EF907DFB4B3E21C1C2256EBCD1 \ ;
HN
public key value (uncompressed)
5A7DED52FCBB097A4ED250E036C7B9C8C7004C4EEDC4F068CD7BF8D3F900E3B4
\
1. 01 05 \ ; HN
public key index 2, Id 05
2. 20
5A8D38864820197C3394B92613B20B91633CBD897119273BF8E4A6F4EEC0A650 \
; HN
public key value
Code 7 - SUCI data sample 2
5.B.2 Default SUCI data on SMAOT500B
The SUCI key can be maximum 64 bytes for Profile
B, and is always 32 bytes for Profile
A.
SUCI uses assymetric cryptos ( Curve25519 and
Secp256r1) not supported in all the old standard 3G/LTE SIM cards in case you
want the SUCI calculation to be made on the UICC. You must generate key pairs
with the above cryptos, the private key goes to the network and the public key
on the cards.
5G
files are under USIM in DF 5FC0 and DF 5FD0. USIM / DF 5FD0 / 4F01
(SUCI_CALC_INFO) is only used if service 125 is activated in UST and should
contain same data as USIM/5FC0/4F07
Please
see information below.
5FC0
4F01;
5GS3GPPLOCI
4F02;
5GSN3GPPLOCI
4F03;
5GS3GPPNSC
4F04;
5GSN3GPPNSC
4F05;
5GAUTHKEYS
4F06;
UAC_AIC
4F07; SUCI_Calc_Info
4F08;
OPL5G
4F09;
NSI
4F0A;
Routing_Indicator
5FD0-SAIP
4F01; SUCI_Calc_Info_USIM
Other
settings to look at are:
Default
Routing Indicator, 4F0A; Routing_Indicator, is F0 FF 00 00, i.e 0, and not
used. If you want to set it to for example 17, then 4F0A = 71 FF 00 00
Note:
Protection Scheme (PS) Identifier 01 (profile A):
Identifier 01 is always Profile A Protection Scheme
(PS) Identifier 02 (profile B): Identifier 02 is always Profile B
Code 8 - Default SUCI data on SMAOT500B
A006020101020000A16B80011B81410472DA71976234CE833A6907425867B82E074D44EF907DF
B4B3E21C1C2256EBCD15A7DED52FCBB097A4ED250E036C7B9C8C7004C4EEDC4F068CD7BF8D3F9
00E3B480011E81205A8D38864820197C3394B92613B20B91633CBD897119273BF8E4A6F4EEC0A
650
Explanatory of the SUCI sample data:
A0, A1, 80 and 81 are "tags" often
(always) followed by a length (in bytes and in Hex format)
A0 : Protection Scheme Identifier List data object tag
06 : Identifier List length (following 6 bytes)
02 01 01 02 00 00 :
Where 02 01 : Protection
Scheme (PS) Identifier 02 (profile B) with Key index 01 (refers to the
first Network Public Key entry in the Home Network Public Key List below),
and 01 02: PS Identifier 01 (profile A)
with Key Index 02 (second Public key entry), and 00 00 : Identifier 00 with Key Index 00 (null scheme)
A1: Home Network Public Key List data
object
6B: Total length from here to end in
bytes (6B = 107 bytes)
80: 01 : 1B (Index
01, length of id, Public Key identifier 1 = 1B i.e 27)
81: 41: 04 Tag for key, Length of data (41 = 65 bytes), flag 04 -> uncompressed
data The public key of key index 1 (Profile B) and identifier 1B (27 in decimal):
72DA71976234CE833A6907425867B82E074D44EF907DFB4B3E21C1C2256EBCD15A7DED52FCBB097A4ED250E
036C7B9C8C7004C4EEDC4F068CD7BF8D3F900E3B4
80: 01: 1E (Index 02, Public key Identifier 2 = 1E i.e. 30)
81: 20: Length of Public Key (20 = 32 bytes)
The
public key of key index 2 (Profile A) and identifier 1E (30 in decimal):
5A8D38864820197C3394B92613B20B91633CBD897119273BF8E4A6F4EEC0A650"
Note for HSS/Core: Home Network Private Key:
C53C22208B61860B06C62E5406A7B330C2B577AA5558981510D128247D38BD1D
Profile B ; ID = 27
Profile A ; ID = 30
Reference:
ECIES test data from 3GPP TS 33.501
5.B.3 Generating SUCI keys with Python
Code 9 - Python code to generate SUCI keys
import nacl.public
from cryptography.hazmat.backends
import default_backend from cryptography.hazmat.primitives.asymmetric import ec from cryptography.hazmat.primitives
import serialization
def generate_suci_keypair(profile):
"""
Generate a SUCI key pair for a specified profile.
Parameters:
profile
(str): 'A' for Curve25519 or 'B' for Secp256r1.
Returns:
tuple:
Private key and public key in hex format. """
if profile == 'A': # Curve25519 using pynacl
(X25519) private_key = nacl.public.PrivateKey.generate()
public_key = private_key.public_key
#
Convert keys to bytes private_key_bytes = bytes(private_key) public_key_bytes =
bytes(public_key)
elif profile == 'B': # Secp256r1 using
cryptography
private_key
= ec.generate_private_key(ec.SECP256R1(),
default_backend()) public_key = private_key.public_key()
# Get raw private key (32 bytes)
private_key_bytes = private_key.private_numbers().private_value.to_bytes(32,
byteorder='big')
#
Get raw public key (64 bytes: 32 bytes X + 32 bytes Y) public_numbers = public_key.public_numbers()
public_key_bytes = public_numbers.x.to_bytes(32, byteorder='big') + public_numbers.y.to_bytes(32, byteorder='big')
else:
raise ValueError("Invalid
profile. Choose 'A' for Curve25519 or 'B' for Secp256r1.")
#
Return private and public keys in hexadecimal format return private_key_bytes.hex(),
public_key_bytes.hex()
def main():
# Generate keys for both Profile A and B
print("Generating SUCI keys for Profile A (Curve25519)...") private_key_A, public_key_A =
generate_suci_keypair('A') print(f"Profile A -
Private Key (Hex): {private_key_A}") print(f"Profile
A - Public Key (Hex): {public_key_A}\n")
print("Generating SUCI keys for Profile B (Secp256r1)...") private_key_B, public_key_B =
generate_suci_keypair('B') print(f"Profile B -
Private Key (Hex): {private_key_B}") print(f"Profile
B - Public Key (Hex): {public_key_B}")
if name ==
" main ": main()
Sample
result
Generating SUCI keys for Profile A (Curve25519)...
Profile
A - Private Key (Hex):
0da28fdeff439431b5f3cc720ea8ffecd96636fd19430f44658d35a49e297503 Profile A -
Public Key (Hex):
0e90c1ce78e707339901b1fc9d6f548a90ef051a50427e2b9a508d75f2794324
Generating
SUCI keys for Profile B (Secp256r1)...
Profile
B - Private Key (Hex):
682c4b886364494462f872918e0bc94eb97c6e10ac3ccf2d73be19f32d1a3eb4 Profile B -
Public Key (Hex):
5b4279b5b501a4852de98957742d806ac6e11898dcaedf448d3e99c295580baa5cfd8374b8ac660f5ab349b64317bb60
7bacee93930c9065735401e674248964
5.C.1 TUAK
For TUAK, the OP key must be extended to 32
bytes—twice the size of the Milenage OP key. Consequently, the resulting OPc
will also be 32 bytes. These keys are to be stored in designated files.
Additionally, you’ll need to use Python to
calculate the correct checksum for the TUAK Ki and OPc keys. The setup also
involves configuring a specific file, and after that, during authentication,
AMF values are used in determining whether to use Milenage or TUAK, adding
complexity to the process.
TUAK configuration parameters are these below
stored in 62F1: 00 7D 10 08 10 10 08 01
-
AMF: `007D`
·
Subscriber
Key (TK) Length: `16 bytes`
·
Message
Authentication Code (MAC) Length: `8 bytes`
·
Confidentiality
Key (CK) Length: `16 bytes`
·
Integrity
Key (IK) Length: `16 bytes`
·
Expected
Result (RES) Length: `8 bytes`
·
Keccak
Iterations: `1`
Pre-personalised TUAK cards has:
TK: 77777777777777777777777777777777
TOP:
00112233445566778899AABBCCDDEEFF00112233445566778899AABBCCDDEEFF
=TOPC:
8836E0D2BBF4FD01A02ED46FEAEB84143E5E8141E1A2978BC5BC84EF17318876
TK
is stored in 62F2
77
77 77 77 77 77 77 77 77 77 77 77 77 77 77 77 A0 33 FF FF FF FF FF FF FF FF FF
FF FF FF FF FF FF FF
Note:
77777777777777777777777777777777 CRC-CCITT (XModem) Checksum: A033
TOPC
is stored in 62F3
01 88 36 E0 D2 BB
F4 FD 01 A0 2E D4 6F EA EB 84 14 3E 5E 81 41 E1 A2 97 8B C5 BC 84 EF
17
31 88 76 CA
EA
Note:
8836E0D2BBF4FD01A02ED46FEAEB84143E5E8141E1A2978BC5BC84EF17318876 CRC-CCITT
(XModem) Checksum: CAEA
5.C.1 URSP User Equipment Route Selection Policy
User
Equipment Route Selection Policy (URSP) is used by the UE to determine how to
route outgoing traffic depending on capabilities expected by an application.
Pre-configured URSP rules are linked to a PLMN and stored in a BER-TLV format
in EFURSP under 5G file system. The coding of the URSP rules is specified in
clause 5.2 and URSP rule is encoded as shown in figures 5.2.1 to 5.2.4 and
table 5.2.1 of 3GPP TS 24.526.
For
example:
|
Example URSP rules |
Comments |
|
|
Rule Precedence =1 |
Route Selection |
This URSP rule associates the traffic of |
|
Traffic Descriptor: |
Descriptor Precedence=1 |
application "App1" with S-NSSAI-a, SSC |
|
Application |
Network Slice Selection: |
Mode 3, 3GPP access and |
|
descriptor=App1 |
S-NSSAI-a SSC Mode Selection: SSC |
the "internet" DNN. It enforces the following routing |
|
Mode 3 |
policy: |
|
|
DNN Selection: internet |
The traffic of App1 should be |
|
|
Access Type preference: |
transferred on a PDU Session supporting |
|
|
3GPP access |
S-NSSAI-a, SSC Mode 3 and DNN=internet |
|
|
over 3GPP access. If this PDU Session is |
||
|
not established, the UE shall attempt to |
||
|
establish a PDU Session with S-NSSAI-a, |
||
|
SSC Mode 3 and the "internet" DNN over |
||
|
3GPP access. |
The
coding would be:
Code 10 - URSP sample code
80
2B
00 F1 10 ; MCC/MNC : 001 01
27
00
25 length
01 ; rule precedence
06
A0 05 41 70 70 31 ; traffic descriptor: OS App Id =
App1
00
1A length
00
18 length
01 ; precedence of route selection descriptor 00 15 ;
length
02
04 01 D1 43 A5 ; S-NSSAI: SST 01 SD D143A5
01 03 ; SSC mode 3
04
09 03 64 6E 6E 04 74 65 73 74; DNN “dnn.test”
10
01; access type: 3GPP access
1.
Glossary
2FF
2nd
Generation Form Factor; the so-called plug-in SIM form factor 3FF
3rd
Generation Form Factor; the so-called microSIM form factor 3GPP
3rd
Generation Partnership Project 4FF
4th
Generation Form Factor; the so-called nanoSIM form
factor A Interface
Interface
between BTS and BSC, traditionally over E1 (3GPP TS 48.008 [3gpp-ts-48- 008])
A3/A8
Algorithm
3 and 8; Authentication and key generation algorithm in GSM and GPRS, typically
COMP128v1/v2/v3 or MILENAGE are typically used
A5
Algorithm
5; Air-interface encryption of GSM; currently only A5/0 (no encryption), A5/1
and A5/3 are in use
Abis Interface
Interface
between BTS and BSC, traditionally over E1 (3GPP TS 48.058 [3gpp-ts-48- 058]
and 3GPP TS 52.021 [3gpp-ts- 52-021])
ACC
Access
Control Class; every BTS broadcasts a bit-mask of permitted ACC, and only subscribers with a SIM
of matching ACC are permitted to use that BTS
AGCH
Access
Grant Channel on Um interface; used to assign a dedicated channel in response
to RACH request
AGPL
GNU
Affero General Public License, a copyleft-style Free Software License AQPSK
Adaptive
QPSK, a modulation scheme used by VAMOS channels on Downlink ARFCN
Absolute
Radio Frequency Channel Number; specifies a tuple of uplink and downlink
frequencies
AUC
Authentication
Center; central database of authentication key material for each subscriber
BCCH
Broadcast
Control Channel on Um interface; used to broadcast information about Cell and
its neighbors
CBC
Cell
Broadcast Centre; central entity of Cell Broadcast service CBCH
Cell
Broadcast Channel; used to transmit Cell Broadcast SMS (SMS-CB) CBS
Cell
Broadcast Service CBSP
Cell
Broadcast Service Protocol (3GPP TS 48.049 [3gpp-ts-48-049]) CC
Call
Control; Part of the GSM Layer 3 Protocol CCCH
Common
Control Channel on Um interface; consists of RACH (uplink), BCCH, PCH, AGCH
(all downlink)
Cell
A cell
in a cellular network, served by a BTS CEPT
Conférence
européenne des administrations des postes et des télécommunications; European
Conference of Postal and Telecommunications Administrations.
CGI
Cell
Global Identifier comprised of MCC, MNC, LAC and BSIC CSFB
Circiut-Switched
Fall Back; Mechanism for switching from LTE/EUTRAN to UTRAN/GERAN when
circuit-switched services such as voice telephony are required.
dB
deci-Bel;
relative logarithmic unit dBm
deci-Bel
(milliwatt); unit of measurement for signal strength of radio signals DHCP
Dynamic
Host Configuration Protocol (IETF RFC 2131 [ietf-rfc2131]) downlink
Direction
of messages / signals from the network core towards the mobile phone DSCP
Differentiated
Services Code Point (IETF RFC 2474 [ietf-rfc2474]) DSP
Digital
Signal Processor dvnixload
Tool
to program UBL and the Bootloader on a sysmoBTS EDGE
Enhanced
Data rates for GPRS Evolution; Higher-speed improvement of GPRS; introduces
8PSK
EGPRS
Enhanced
GPRS; the part of EDGE relating to GPRS services EIR
Equipment
Identity Register; core network element that stores
and manages IMEI numbers
ESME
External
SMS Entity; an external application interfacing with a SMSC over SMPP ETSI
European
Telecommunications Standardization Institute FPGA
Field
Programmable Gate Array; programmable digital logic hardware Gb
Interface
between PCU and SGSN in GPRS/EDGE network; uses NS, BSSGP, LLC GERAN
GPRS/EDGE
Radio Access Network GGSN
GPRS
Gateway Support Node; gateway between GPRS and external (IP) network GMSK
Gaussian
Minimum Shift Keying; modulation used for GSM and GPRS
GPL
GNU
General Public License, a copyleft-style Free Software License Gp
Gp
interface between SGSN and GGSN; uses GTP protocol GPRS
General
Packet Radio Service; the packet switched 2G
technology GPS
Global
Positioning System; provides a highly accurate clock reference besides the
global position
GSM
Global
System for Mobile Communications. ETSI/3GPP Standard of a 2G digital cellular
network
GSMTAP
GSM
tap; pseudo standard for encapsulating GSM protocol layers over UDP/IP for
analysis
GSUP
Generic
Subscriber Update Protocol. Osmocom-specific alternative to TCAP/MAP
GT GTP
HLR
Global
Title; an address in SCCP
GPRS Tunnel Protocol; used between SGSN and GGSN
Home
Location Register; central subscriber database of a GSM network HNB-GW
Home
NodeB Gateway. Entity between femtocells (Home NodeB) and CN in 3G/UMTS. HPLMN
Home
PLMN; the network that has issued the subscriber SIM and has his record in HLR
IE
Information
Element IMEI
International
Mobile Equipment Identity; unique 14-digit decimal
number to globally identify a mobile device, optionally with a 15th checksum
digit
IMEISV
IMEI
software version; unique 14-digit decimal number to globally identify a mobile
device (same as IMEI) plus two software version digits (total digits: 16)
IMSI
International
Mobile Subscriber Identity; 15-digit unique identifier for the subscriber/SIM;
starts with MCC/MNC of issuing operator
IP IPA
Iu IuCS IuPS LAC
Internet Protocol (IETF RFC 791 [ietf-rfc791])
ip.access GSM over
IP protocol; used to multiplex a single TCP connection Interface in 3G/UMTS
between RAN and CN
Iu interface for circuit-switched domain. Used in
3G/UMTS between RAN and MSC Iu interface for packet-switched domain. Used in
3G/UMTS between RAN and SGSN Location Area Code; 16bit identifier of Location
Area within network
LAPD
Link
Access Protocol, D-Channel (ITU-T Q.921 [itu-t-q921]) LAPDm
Link
Access Protocol Mobile (3GPP TS 44.006 [3gpp-ts-44-006]) LLC
Logical
Link Control; GPRS protocol between MS and SGSN (3GPP TS 44.064 [3gpp-ts-
44-064])
Location Area
Location
Area; a geographic area containing multiple BTS LU
Location
Updating; can be of type IMSI-Attach or Periodic. Procedure that indicates a
subscriber’s physical presence in a given radio cell.
M2PA
MTP2
Peer-to-Peer Adaptation; a SIGTRAN Variant (RFC 4165 [ietf-rfc4165]) M2UA
MTP2
User Adaptation; a SIGTRAN Variant (RFC 3331 [ietf-rfc3331]) M3UA
MTP3
User Adaptation; a SIGTRAN Variant (RFC 4666 [ietf-rfc4666]) MCC
Mobile
Country Code; unique identifier of a country, e.g. 262 for Germany MFF
Machine-to-Machine
Form Factor; a SIM chip package that is soldered permanently onto M2M device
circuit boards.
MGW
Media
Gateway MM
Mobility
Management; part of the GSM Layer 3 Protocol MNC
Mobile
Network Code; identifies network within a country; assigned by national
regulator
MNCC
Mobile
Network Call Control; Unix domain socket
based Interface between MSC and external call control entity like
osmo-sip-connector
MNO
Mobile Network Operator; operator with physical
radio network under his MCC/MNC
MO MS MSC
Mobile
Originated. Direction from Mobile (MS/UE) to Network Mobile Station; a mobile
phone / GSM Modem
Mobile
Switching Center; network element in the circuit-switched core network MSC pool
A number of
redundant MSCs serving the same core network, which a BSC / RNC distributes
load across; see also the "MSC Pooling" chapter in OsmoBSC’s user
manual [userman-osmobsc] and 3GPP TS 23.236 [3gpp-ts-23-236]
MSISDN
Mobile
Subscriber ISDN Number; telephone number of the subscriber MT
Mobile
Terminated. Direction from Network to Mobile (MS/UE) MTP
Message
Transfer Part; SS7 signaling protocol (ITU-T Q.701 [itu-t-q701]) MVNO
Mobile
Virtual Network Operator; Operator without physical radio network NCC
Network
Color Code; assigned by national regulator NITB
Network
In The Box; combines functionality traditionally
provided by BSC, MSC, VLR, HLR, SMSC functions; see OsmoNITB
NRI
Network
Resource Indicator, typically 10 bits of a TMSI indicating which MSC of an MSC
pool attached the subscriber; see also the "MSC Pooling" chapter in
OsmoBSC’s user manual [userman-osmobsc] and 3GPP TS 23.236 [3gpp-ts-23- 236]
NSEI
NS
Entity Identifier NVCI
NS
Virtual Circuit Identifier NWL
Network
Listen; ability of some BTS to receive downlink from other BTSs NS
Network
Service; protocol on Gb interface (3GPP TS 48.016 [3gpp-ts-48-016]) OCXO
Oven
Controlled Crystal Oscillator; very high precision oscillator, superior to a
VCTCXO
OML
Operation
& Maintenance Link (ETSI/3GPP TS 52.021 [3gpp-ts-52-021]) OpenBSC
Open Source
implementation of GSM network elements, specifically OsmoBSC, OsmoNITB,
OsmoSGSN
OpenGGSN
Open Source
implementation of a GPRS Packet Control Unit OpenVPN
Open-Source
Virtual Private Network; software employed to establish encrypted private
networks over untrusted public networks
Osmocom
Open Source MObile
COMmunications; collaborative community for implementing communications
protocols and sys- tems, including GSM, GPRS, TETRA, DECT, GMR and others
OsmoBSC
Open Source
implementation of a GSM Base Station Controller OsmoNITB
Open Source
implementation of a GSM Network In The
Box, combines functionality traditionally provided by BSC, MSC, VLR, HLR, AUC,
SMSC
OsmoSGSN
Open Source
implementation of a Serving GPRS Support Node OsmoPCU
Open Source
implementation of a GPRS Packet Control Unit OTA PC PCH PCP PCU
Over-The-Air;
Capability of operators to remotely reconfigure/reprogram ISM/USIM cards Point
Code; an address in MTP
Paging
Channel on downlink Um interface; used by network to page an MS Priority Code
Point (IEEE 802.1Q [?])
Packet
Control Unit; used to manage Layer 2 of the GPRS radio interface PDCH
Packet
Data Channel on Um interface; used for GPRS/EDGE signalling + user data PIN
Personal
Identification Number; a number by which the user
authenticates to a SIM/USIM or other smart card
PLMN
Public
Land Mobile Network; specification language for a single GSM network PUK
PIN
Unblocking Code; used to unblock a blocked PIN (after too many wrong PIN
attempts)
RAC
Routing
Area Code; 16bit identifier for a Routing Area within a Location Area RACH
Random
Access Channel on uplink Um interface; used by MS to request establishment of a
dedicated channel
RAM
Remote
Application Management; Ability to remotely manage
(install, remove) Java Applications on SIM/USIM Card
RF
Radio
Frequency RFM
Remote
File Management; Ability to remotely manage (write,
read) files on a SIM/USIM card
Roaming
Procedure
in which a subscriber of one network is using the radio network of another
network, often in different countries; in some countries national roaming
exists
Routing Area
Routing
Area; GPRS specific sub-division of Location Area RR RSL RTP
Radio
Resources; Part of the GSM Layer 3 Protocol Radio Signalling Link (3GPP TS
48.058 [3gpp-ts-48-058])
Real-Time
Transport Protocol (IETF RFC 3550 [ietf-rfc3550]); Used to transport
audio/video streams over UDP/IP
SACCH
Slow
Associate Control Channel on Um interface; bundled to a TCH or SDCCH, used for
signalling in parallel to active dedicated channel
SCCP
Signaling
Connection Control Part; SS7 signaling protocol (ITU-T Q.711 [itu-t- q711])
SDCCH
Slow
Dedicated Control Channel on Um interface; used for signalling and SMS
transport in GSM
SDK
Software
Development Kit SGs
Interface
between MSC (GSM/UMTS) and MME (LTE/EPC) to facilitate CSFB and SMS. SGSN
Serving
GPRS Support Node; Core network element for packet-switched services in GSM and
UMTS.
SIGTRAN
Signaling
Transport over IP (IETF RFC 2719 [ietf-rfc2719]) SIM
Subscriber
Identity Module; small chip card storing subscriber identity Site
A site
is a location where one or more BTSs are installed, typically three BTSs for
three sectors
SMPP
Short
Message Peer-to-Peer; TCP based protocol to interface external entities with an
SMSC
SMSC
Short
Message Service Center; store-and-forward relay for short messages SS7 SS
Signaling System No. 7; Classic digital
telephony signaling system
Supplementary Services;
query and set various service parameters between subscriber and core network
(e.g. USSD, 3rd-party calls, hold/retrieve, advice-of-charge, call deflection)
SSH SSN STP SUA
Secure Shell; IETF RFC 4250 [ietf-rfc4251] to 4254
Sub-System
Number; identifies a given SCCP Service such as MSC, HLR Signaling Transfer
Point; A Router in SS7 Networks
SCCP
User Adaptation; a SIGTRAN Variant (RFC 3868 [ietf-rfc3868]) syslog
System
logging service of UNIX-like operating systems System Information
A set
of downlink messages on the BCCH and SACCH of the Um interface describing
properties of the cell and network
TCH
Traffic
Channel; used for circuit-switched user traffic (mostly voice) in GSM TCP
Transmission
Control Protocol; (IETF RFC 793 [ietf-rfc793]) TFTP
Trivial
File Transfer Protocol; (IETF RFC 1350 [ietf-rfc1350]) TOS TRX TS
Type
Of Service; bit-field in IPv4 header, now re-used as DSCP (IETF RFC 791 [ietf-
rfc791]) Transceiver; element of a BTS serving a single carrier
Technical
Specification u-Boot
Boot
loader used in various embedded systems UBI UBL UDP
An MTD
wear leveling system to deal with NAND flash in Linux Initial bootloader loaded
by the TI Davinci SoC
User
Datagram Protocol (IETF RFC 768 [ietf-rfc768]) UICC
Universal
Integrated Chip Card; A smart card according to ETSI TR 102 216 [etsi-
tr102216]
Um interface
U
mobile; Radio interface between MS and BTS uplink
Direction
of messages: Signals from the mobile phone towards the network USIM
Universal
Subscriber Identity Module; application running on a UICC to provide subscriber
identity for UMTS and GSM networks
USSD
Unstructured
Supplementary Service Data; textual dialog between subscriber and core network,
e.g. *100 ? Your exten- sion is 1234
VAMOS
Voice
services over Adaptive Multi-user channels on One Slot; an optional extension
for GSM specified in Release 9 of 3GPP GERAN specifications (3GPP TS 48.018
[3gpp- ts-48-018]) allowing two independent UEs to transmit and receive
simultaneously on traffic channels
VCTCXO
Voltage
Controlled, Temperature Compensated Crystal Oscillator; a precision oscillator,
superior to a classic crystal oscil- lator, but inferior to an OCXO VLAN
Virtual
LAN in the context of Ethernet (IEEE 802.1Q [ieee-802.1q]) VLR
Visitor
Location Register; volatile storage of attached subscribers in the MSC VPLMN
Visited
PLMN; the network in which the subscriber is currently registered; may differ
from HPLMN when on roaming
VTY
Virtual
TeletYpe; a textual command-line interface for configuration and introspection,
e.g. the OsmoBSC configuration file as well as its telnet link on port 4242